Veza Alternatives
The Best Veza Alternatives & Competitors for 2026

Veza Alternatives

The High-Intelligence, Low-Barrier IGA Alternative
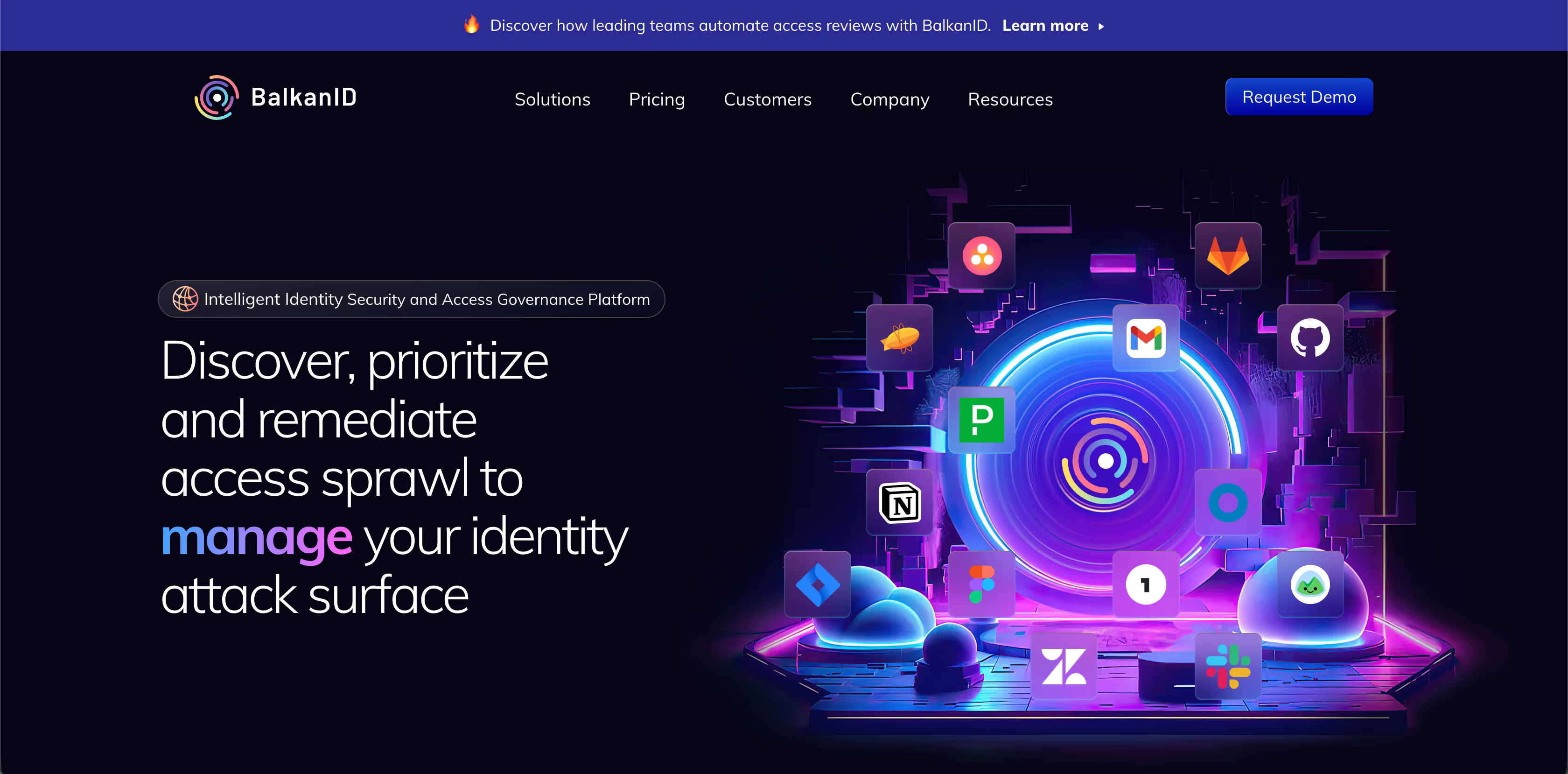
BalkanID is built for organizations that need true identity governance without enterprise friction. Positioned as the first Intelligent IGA, BalkanID focuses on identifying, explaining, and remediating risky entitlements across SaaS, cloud, and on-prem environments—bridging the gap between basic access management tools and heavyweight identity security platforms like Veza.
Rather than modeling access for its own sake, BalkanID is designed to help security and compliance teams make faster, higher-confidence access decisions.
Security and Compliance teams (SMB to Enterprise) that:
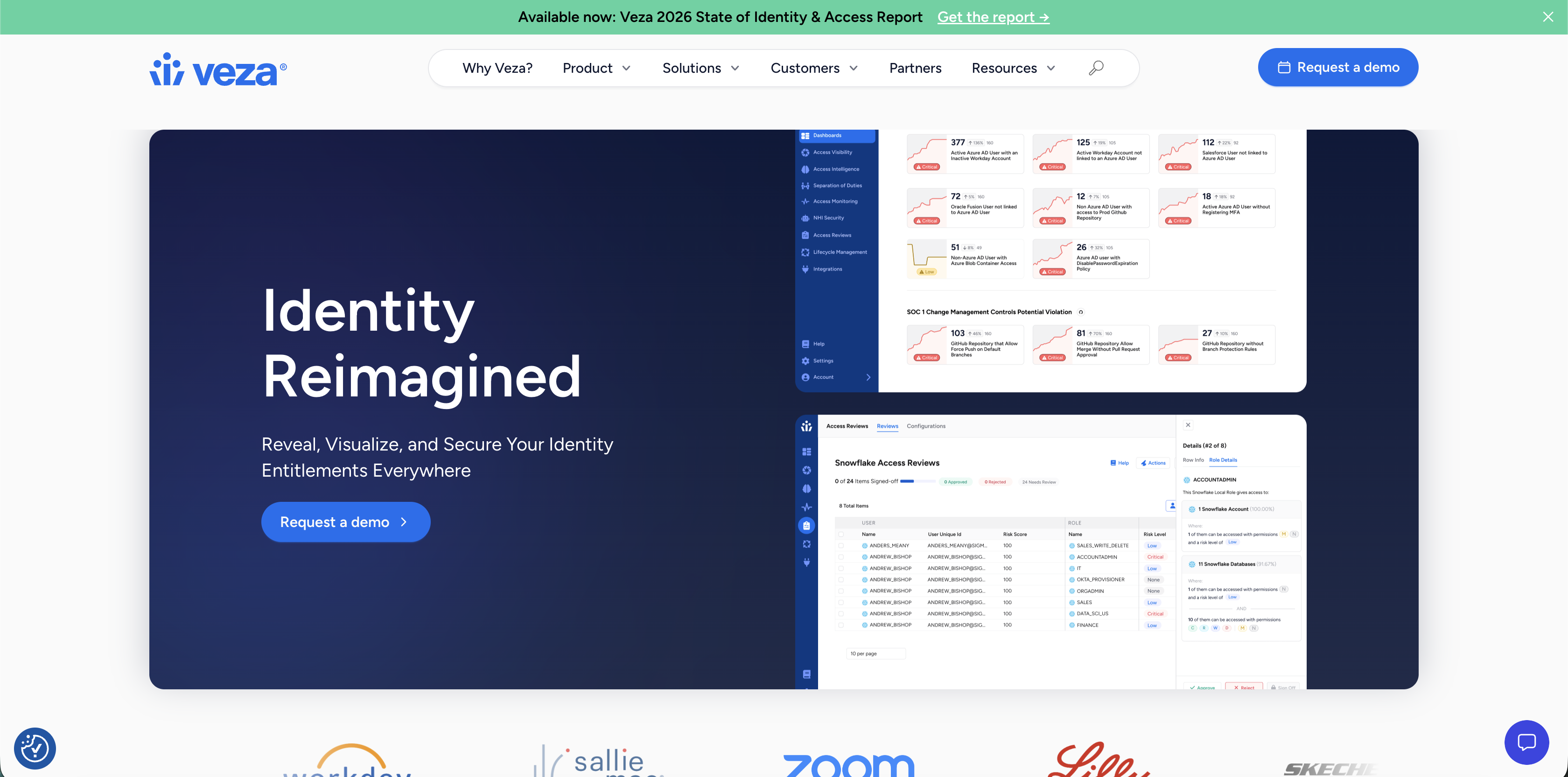
Veza positions itself as “the authorization platform for data”, built to help large enterprises understand effective permissions across cloud, SaaS, and data systems. At the core of the platform is Veza’s Access Graph, which models the relationships between identities (human and non-human), resources, and permissions.
Veza excels in environments where data access complexity and scale demand extremely granular visibility.
Large enterprises with:
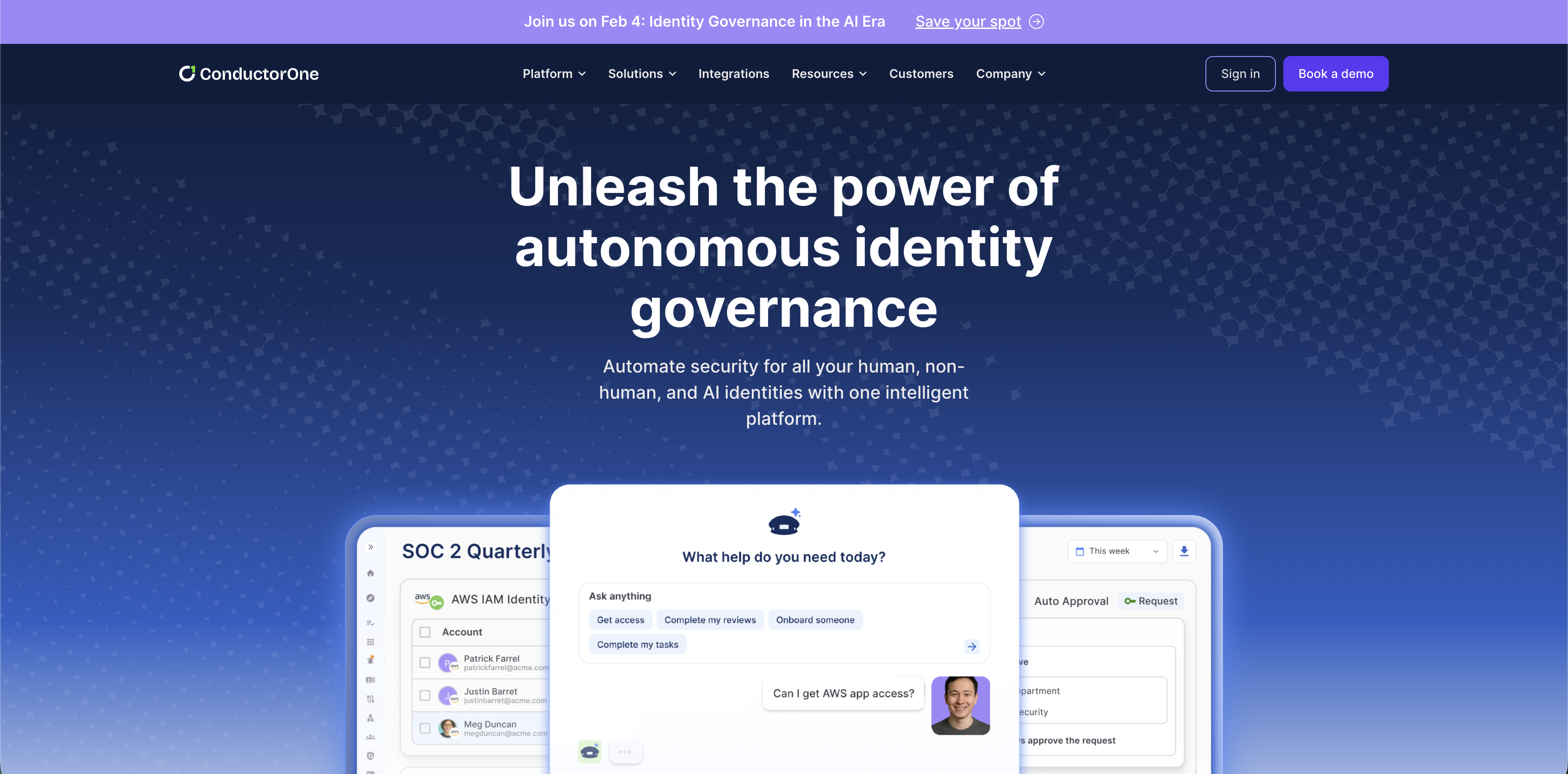
ConductorOne is an AI-native identity security platform built for large organizations managing the rapid growth of human, non-human, and AI identities across cloud and on-prem systems. Its core mission is to minimize the number of identity tasks humans need to touch, using automation, policy, and orchestration.
The platform emphasizes access requests, lifecycle automation, and just-in-time access, with governance embedded into operational workflows.
Large, high-growth enterprises that:

Zilla Security positions itself as a modern, AI-driven Identity Governance platform, designed to replace legacy IGA tools with faster deployment, automation, and improved usability. Zilla focuses on cloud-first environments, emphasizing AI-powered access reviews, role mining, and lifecycle governance with a strong user experience.
Zilla is often seen as a next-generation alternative to SailPoint, targeting organizations that want enterprise-grade governance without the traditional IGA implementation burden.
Mid-to-large enterprises that:
Book a Demo with BalkanID today and see how effortless compliance can be.